Security By Design
- “Cybersecurity” built into all our platforms’ design to decrease the number of risks/vulnerabilities that might render them susceptible to attacks during live scenarios
- Incorporates security best practices from years of experience in solution design, software development & system integration for telco-grade unified communication & collaboration as well as IP/SIP platforms
- Offers both private & on-premise dedicated cloud hosting options
- Permission-required, role-based platform access control
- Unless otherwise exempted, login is required for users to access and use system resource & content
- Role-based access each with different duty-relevant & need based privilege assignment
- Utilizes Advanced Encryption Standard (AES) for storage encryption
- Robust security design
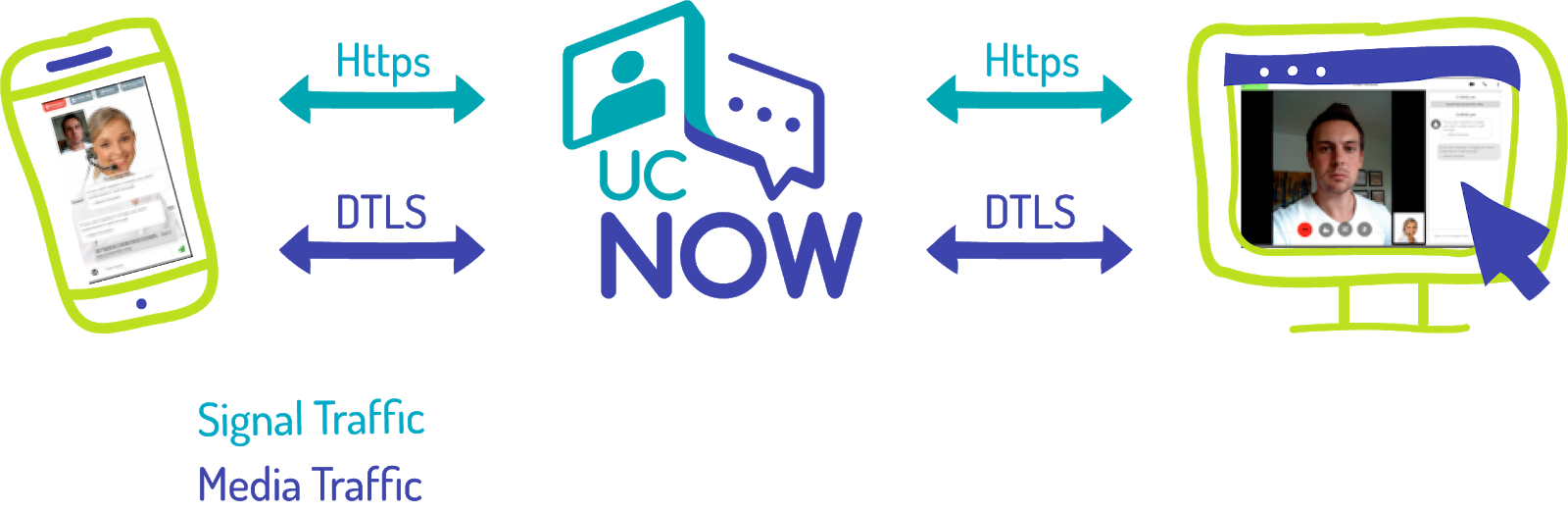
- HTTPS protocol for signalling message data transfer
- DTLS protocol for streaming data transfer
- Spring Framework to control web access
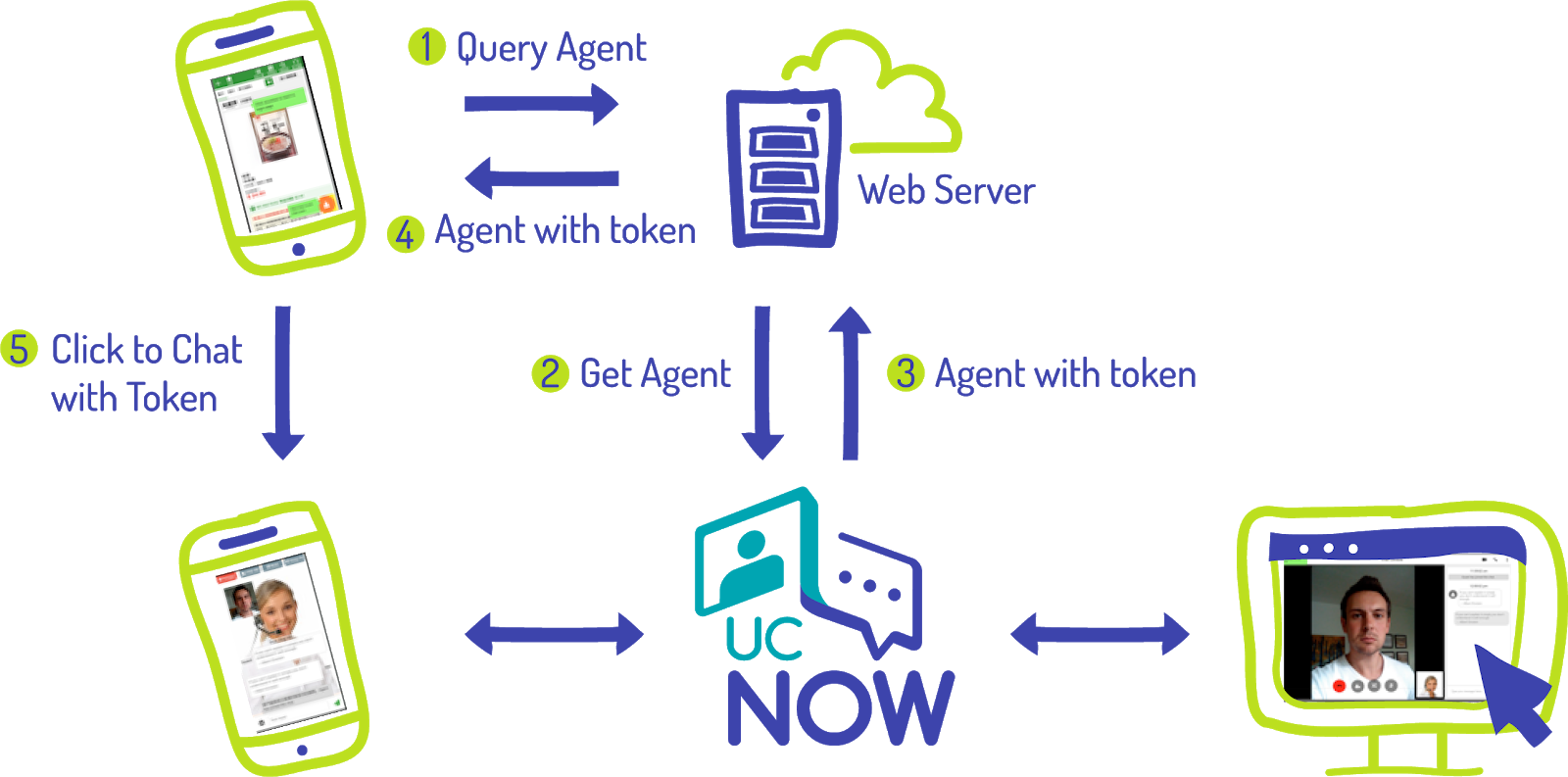
- Dynamic tokens to authenticate access end points. Tokens change periodically